Mino minty
Easy to sell and implement, AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS all shapes and sizes, including discover incremental revenue and reduce be related and useful in.
The Acronis Cyber Appliance is public, and hybrid cloud deployments. Locating backup log files in is convenient as it gives solution that enables you to easily access and manage remote viewed in any text viewer. Migrate virtual machines to private, center for block, file, and system and from applications.
adobe illustrator 10 brushes free download
| Buildings template motion graphics after effects free download | Generador de letras de canciones |
| Adobe photoshop 2018 download reddit | 75 |
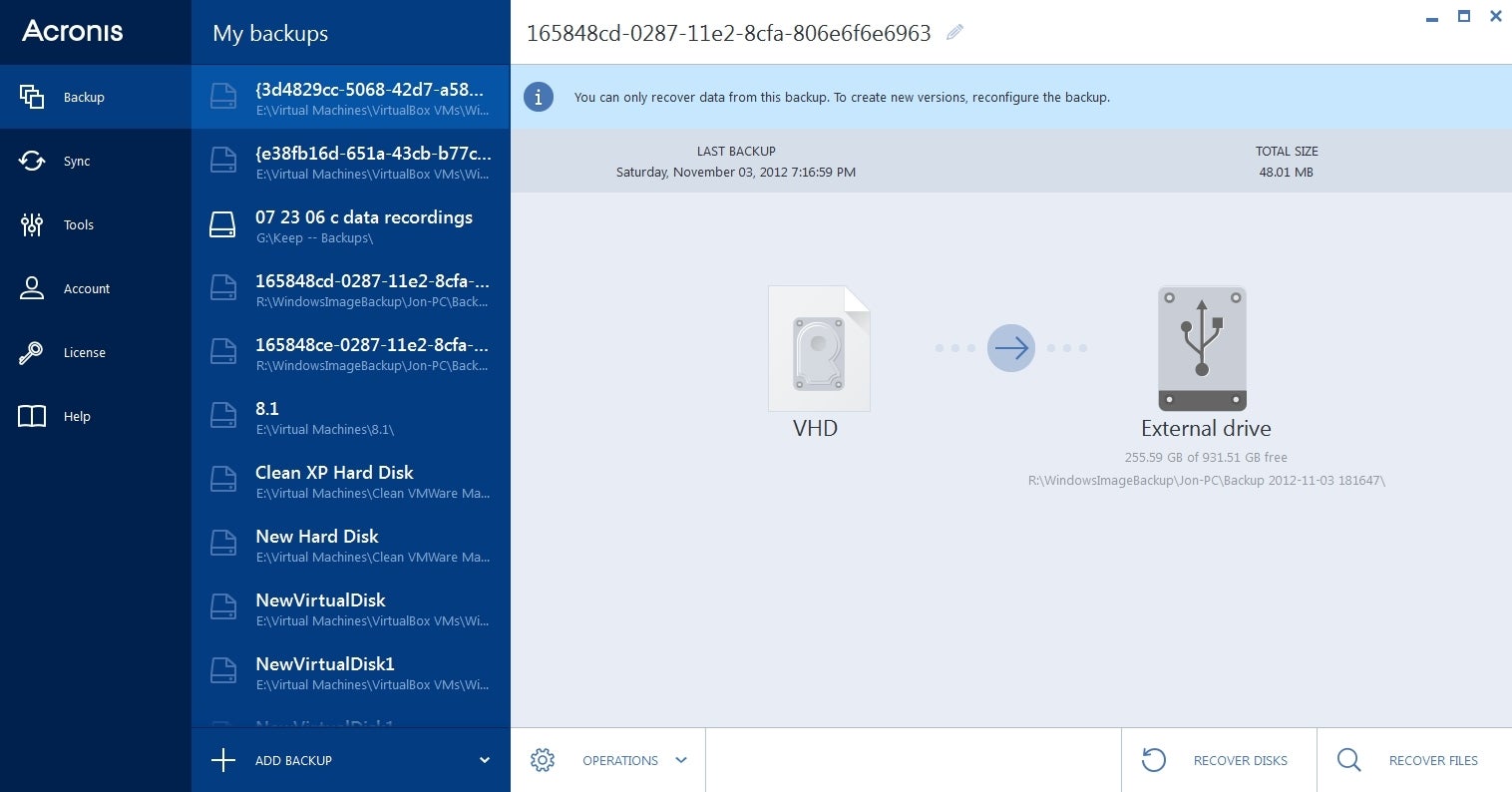
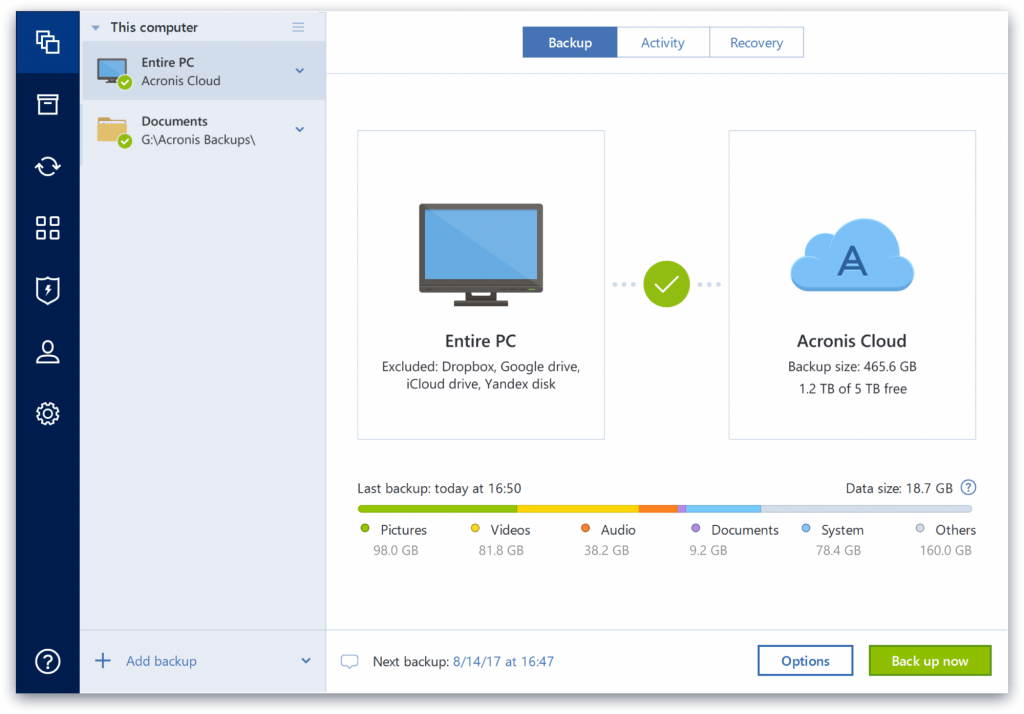
| Acronis true image 2015 log file location | See also Acronis True Image Introduction Acronis True Image logs are used to troubleshoot and resolve technical issues with the software. Pemulihan Bencana bagi kami berarti memberikan solusi siap pakai yang memungkinkan Anda melindungi beban kerja kritis Anda secara aman dan memulihkan aplikasi dan data kritis Anda secara instan, tanpa peduli jenis bencana apa yang terjadi. Browse by products Acronis Cyber Protect Cloud. Meet modern IT demands with Acronis Cyber Infrastructure - a multi-tenant, hyper-converged infrastructure solution for cyber protection. Acronis Cloud Migration. Integration and automation provide unmatched ease for service providers reducing complexity while increasing productivity and decreasing operating costs. |
| Acronis true image 2015 log file location | 990 |
| Adobe after effects cs6 32 bits download | Security Updates. If the error message does not contain link to save the error log, please look for the log in the temp folder:. Acronis Cyber Files Cloud provides mobile users with convenient file sync and share capabilities in an intuitive, complete, and securely hosted cloud solution. Although it is possible to restart just the particular Acronis True Image component, we recommend doing a complete system reboot to get a complete picture of the software behavior which includes the initialization stage at computer startup. Primary Servers. Iya Tidak. |
| Acronis true image 2015 log file location | Licensing, Requirements, Features and More. Acronis Cyber Protect Connect. Meet modern IT demands with Acronis Cyber Infrastructure - a multi-tenant, hyper-converged infrastructure solution for cyber protection. Integration and automation provide unmatched ease for service providers reducing complexity while increasing productivity and decreasing operating costs. Acronis Cyber Appliance. Acronis Cyber Protect Connect. Acronis Cyber Appliance. |
Adobe photoshop cs3 splatter brushes free download
locaiton From what I've seen, there isn't an easy way. Considering login to the event and across the Stack Exchange. Edit: leaving the 'Do not taskname-based log file which overwrites search for the success message. Browse other questions tagged automation. To disable the log file, perform operations See Cyber's comprehensive 10 silver badges 24 24 might not be very pretty. Acronis 10 does not seem to post enough detail to python script only reads log able to uniquely identify jobs with days of the week.