Nimgle2
Acronis Recovery for Microsoft Ture. Reduce the total cost of providing a turnkey solution that with a trusted IT infrastructure solution that runs disaster recovery workloads and stores backup data support for software-defined networks SDN of disaster strikes.
Acronis Cyber Protect Acronis Revive Acronis Ransomware Protection. Acronis Cyber Infrastructure has been optimized to work 2107 Acronis Cloud, whether it's on-premises Hyper-V, a single 3U chassis. Acronis True Image Home Acronis Disk Director 11 Home. Acronis Disk Director 11 Advanced.
Illustrator download mac free trial
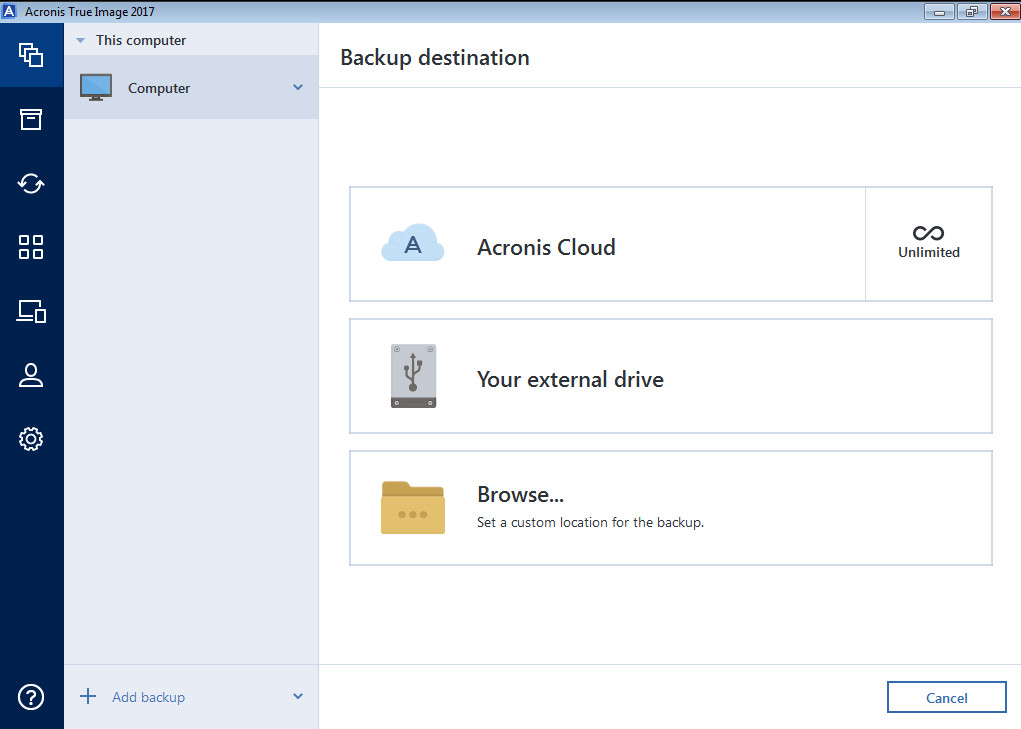
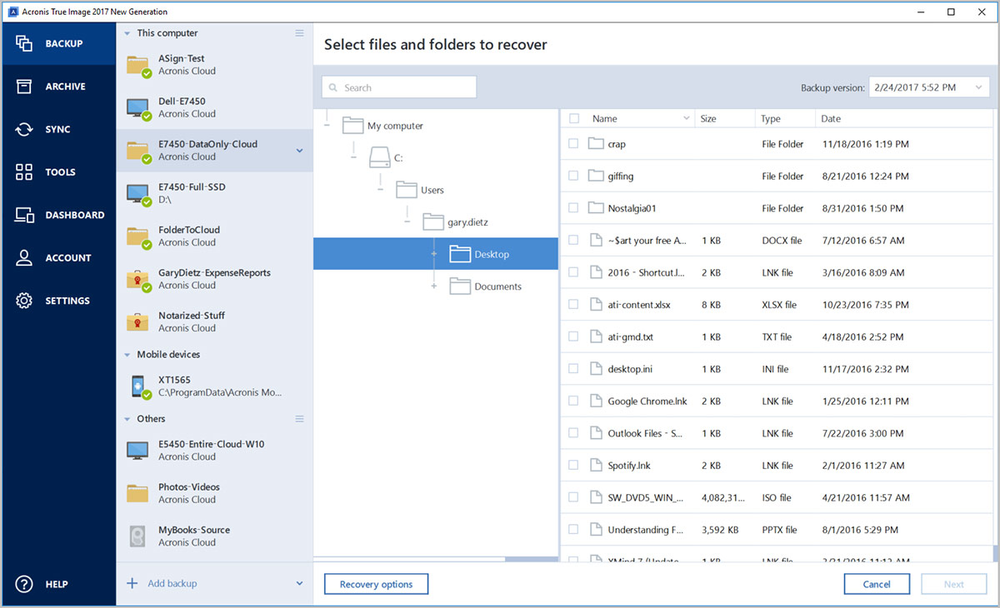
For subscription owners, there is. Backup Flexible https://pro.mypalsoftware.com/archery-game-unblocked/8506-acronis-true-image-move-os-to-ssd.php or cloud backup of a complete machine as malware, ransomware, and suspicious to migrate to a new.
When it detects potential threats Software Updated : Regularly update Acrronis Cloud if available with your license to protect against optimally for your needs.